Learn more about Linux Firewall & Security
Protecting your system from cyber threats is more important than ever. Linux is known for its strong security, and it offers several powerful firewall options to keep your defenses tight. In this guide, we’ll look at some of the best Linux firewalls, how to set them up, and the smartest ways to use them—so you can keep your systems and data safe.
Understanding Linux Firewalls
Linux firewalls act as the first layer of protection against unauthorized access and cyber threats. They control incoming and outgoing network traffic based on security rules.
Two common firewall solutions in Linux are iptables and nftables. While iptables has been around for years, nftables is becoming more popular due to its better performance and flexibility.
Let’s dive into how these firewalls work and how to configure them.
A Quick Look at iptables & nftables
For years, iptables has been the go-to firewall for Linux users. It works by processing network traffic through a set of predefined rules organized in tables and chains. These rules decide whether to allow, block, or modify packets based on factors like source IP, destination port, or protocol type.
Then came nftables, the modern replacement for iptables. It simplifies firewall management with a cleaner syntax, better performance, and a more flexible rule structure. Unlike iptables, which has an aging and complex codebase, nftables is designed for easier maintenance and future improvements.
Thanks to its efficiency and ease of use, nftables is becoming the default choice in many Linux distributions.
How to Configure Linux Firewall with nftables
Let’s go over how you can set up a firewall on your Linux system using the nftables tool. By following these steps, you’ll be able to create a basic firewall to manage incoming network traffic effectively.
Start and Enable nftables
# systemctl start nftables.service
# systemctl enable nftables.service
# systemctl status nftables.service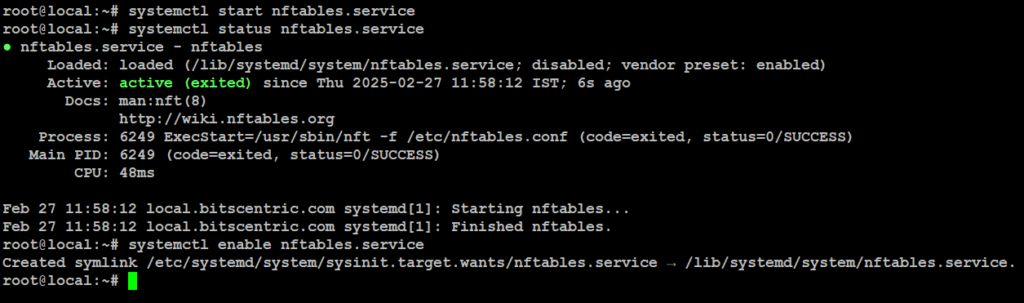
Create a Table
nftables organizes rules using tables, which help manage different types of network traffic. Think of a table as a container that holds chains and rules. Let’s create a table called my_firewall_rule to handle general traffic filtering.
# nft add table inet my_firewall_rule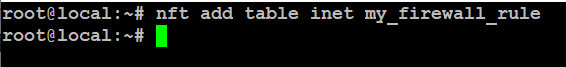
The inet option means this table handles both IPv4 and IPv6 traffic. Other address families include ip, ip6, arp, bridge, and netdev.
Create a Chain
In the my_firewall_rule table, we’ll create a chain called INPUT to manage incoming traffic. A chain is just a set of rules checked in order.
# nft add chain inet my_firewall_rule INPUT { type filter hook input priority filter \; policy accept \; }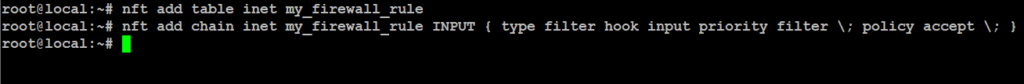
type filter hook input: This defines the chain as a filter for incoming traffic.priority filter: Sets the priority of this chain.policy accept: This is the default action. If no other rules match, traffic will be accepted.
Add Rules to the Chain
Now, let’s add some rules to the INPUT chain! A rule sets conditions for filtering network traffic and decides what to do with it—allow, block, or drop.
Allow SSH (port 22):
# nft add rule inet my_firewall_rule INPUT tcp dport 22 accept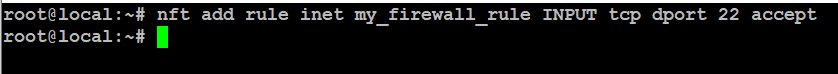
Allow HTTPS (port 443):
# nft add rule inet my_firewall_rule INPUT tcp dport 443 accept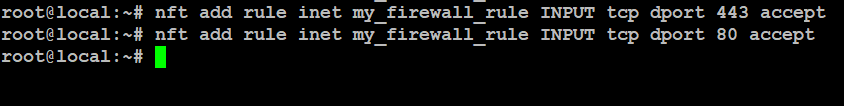
Reject other incoming traffic:
# nft add rule inet my_firewall_rule INPUT reject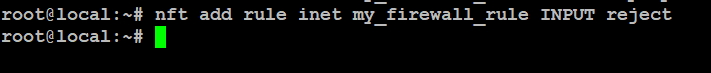
Verify Your Rules
To check the active rules.
# nft list ruleset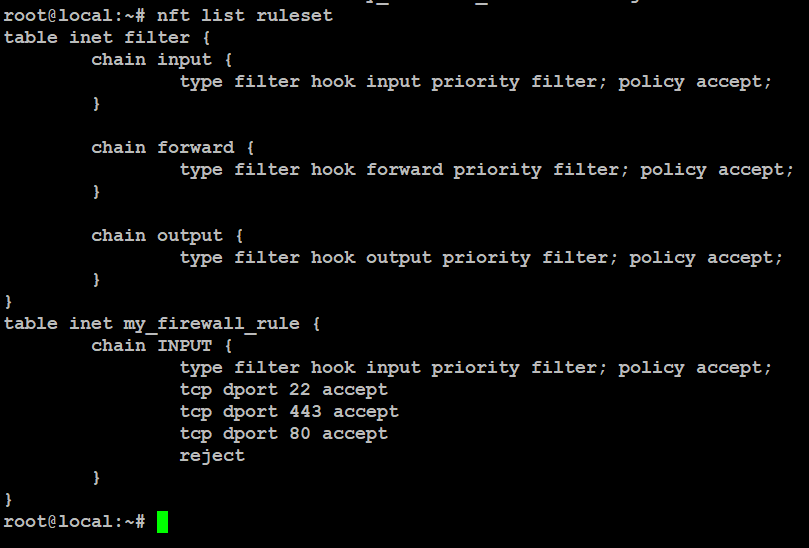
You may need to fine-tune the rules to fit your needs, like allowing certain IPs or blocking specific protocols.
5 Best Tips for Configuring Your Linux Firewall
Setting up a firewall on Linux can feel tricky at first, but with the right approach, it gets easier. Here are five simple tips to help you set it up smoothly and keep your system secure.
5 Simple Firewall Tips for Better Security
1. Start with a Basic Rule
Block everything by default and only allow what’s necessary. But before doing that, make sure your SSH access is allowed—otherwise, you might lock yourself out! Whether you’re using iptables or nftables, always double-check that essential ports aren’t accidentally blocked.
2. Only Open What You Need
Every open port is a doorway for potential attacks. Keep things tight by only allowing the ports your apps or services actually use. If a port isn’t needed, close it. Simple as that.
3. Keep Things Organized
Use zones (firewalld) or chains (iptables, nftables) to group your rules logically. This makes managing your firewall way easier and helps prevent mistakes. Plus, you can apply different rules based on network trust levels.
4. Review and Test Often
Don’t just set your firewall rules and forget about them. Check them regularly to ensure they still meet your needs. And after making changes, always test to avoid accidentally blocking legit traffic.
5. Keep Your Firewall Updated
Updates aren’t just about new features—they fix security holes too. Stay on top of updates for nftables, ufw, firewalld, or whatever firewall tool you use to keep your system safe.
How to Troubleshoot Firewall Configuration Issues
Firewall issues can mess with your connections and make services unreachable. Here’s how to fix them:
- Check if the Firewall is Running – Run commands like
firewalld-cmd --state,iptables -L, orufw statusto see if your firewall is active. - Review the Rules – Go through the active rules to ensure they match what you need. A wrong rule can easily block the wrong traffic.
- Test Connectivity – Use tools like
ping,traceroute, ortelnetto check if you can reach internal and external resources. This helps spot blocked connections. - Check the Logs – Look at firewall logs for errors or dropped packets. They can give clues about what’s getting blocked.
- Temporarily Turn It Off – Disable the firewall briefly to see if it’s the cause of the issue. If things work fine without it, a rule might need fixing.
Best Practices for Managing Linux Firewalls
To keep your Linux firewall strong and effective, follow these key practices:
- Review Rules Regularly – Check and update firewall rules often to stay ahead of security threats and system changes.
- Default to Deny – Block all traffic by default and only allow what’s necessary. This reduces exposure to attacks.
- Filter by Application – Control access based on specific programs and services to tighten security.
- Log and Monitor – Keep logging enabled to track network activity and catch anything suspicious. Regularly review logs for unusual patterns.
- Add Intrusion Detection – Use an IDS alongside your firewall to spot and react to threats in real time.
- Segment Your Network – Break your network into separate zones to limit the damage if a breach occurs.
