How to Configure Samba4 as an Active Directory on Ubuntu 24.04
Samba is a free and open-source software that enables seamless interoperability between Windows and Linux/Unix operating systems.
It can function as a standalone file and print server for both Windows and Linux clients using the SMB/CIFS protocol suite. Additionally, Samba can serve as an Active Directory (AD) Domain Controller or be joined to a domain as a member within a realm. Currently, Samba 4 supports emulating an AD Domain Controller up to the Windows 2008 R2 domain and forest functional levels.
I’ll start by walking you through all the steps you need to follow to install and configure Samba4 as a Domain Controller.
Initial Configuration for Samba4
Before starting the Samba4 AD DC installation, ensure your system is fully updated with the latest security patches, kernel updates, and packages.
# apt-get update
# apt-get upgrade
# apt-get dist-upgrade
Install Required Packages for Samba4 AD DC
To set up your server as an Active Directory Domain Controller, install Samba along with all the necessary packages on your system.
# apt-get install samba krb5-user krb5-config winbind libpam-winbind libnss-winbind
During the installation process, the installer will ask several questions to help configure the domain controller.
On the first screen, you’ll need to specify the default REALM name for Kerberos in uppercase. Enter the name of your domain in uppercase, then press Enter to proceed.

Finally, enter the hostname for the administrative server of your Kerberos realm. You can use your domain name for this. Press Enter to complete the installation.

Ensure the hostname for the administrative server of your Kerberos realm matches your domain name. Once confirmed, press Enter to complete the installation.

Complete install all package.

Provision Samba AD DC for Your Domain
Before configuring Samba for your domain, make sure to run the following commands to stop and disable all Samba daemons.
# systemctl stop samba-ad-dc.service smbd.service nmbd.service winbind.service
# systemctl disable samba-ad-dc.service smbd.service nmbd.service winbind.service
Next, rename or remove the original Samba configuration file. This step is essential before provisioning Samba AD, as Samba will create a new configuration file from scratch during the provisioning process. If it detects an existing smb.conf file, it will cause errors.
# mv /etc/samba/smb.conf /etc/samba/smb.conf.initial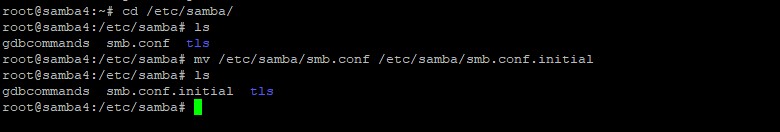
To begin the domain provisioning process, run the following command with root privileges and accept the default options provided by Samba.
Be sure to provide the IP address for a DNS forwarder (either internal or external), and choose a strong password for the Administrator account. If you select a weak password, the domain provisioning will fail.
# samba-tool domain provision --use-rfc2307 --interactive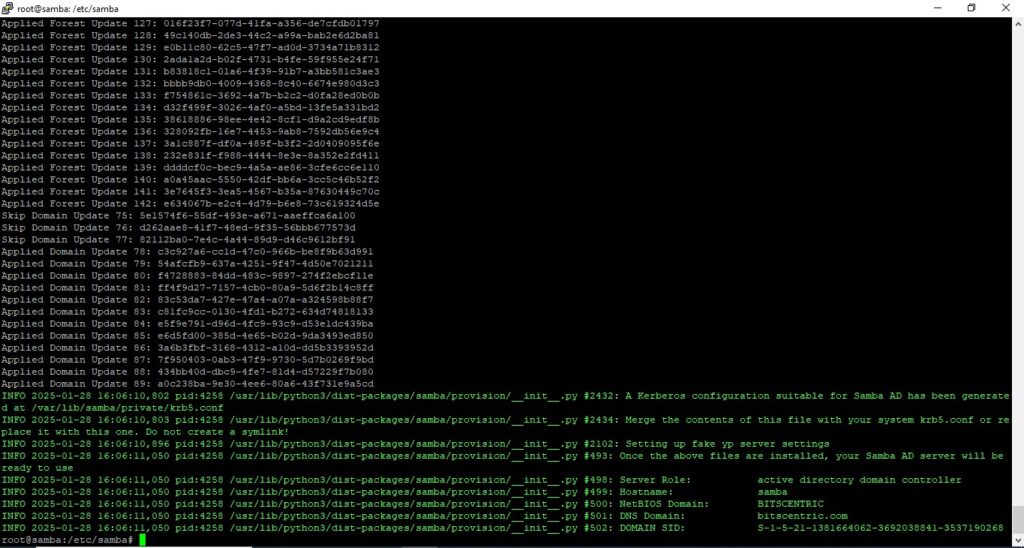
Rename or remove the main Kerberos configuration file from the /etc directory, then replace it with a symbolic link pointing to the newly generated Kerberos file located in the /var/lib/samba/private directory by running the following commands:
# mv /etc/krb5.conf /etc/krb5.conf.initial
# ln -s /var/lib/samba/private/krb5.conf /etc/
# ls -l /etc/krb5.conf
Start and enable Samba Active Directory Domain Controller daemons
# systemctl start samba-ad-dc.service
# systemctl enable samba-ad-dc.service
# systemctl status samba-ad-dc.service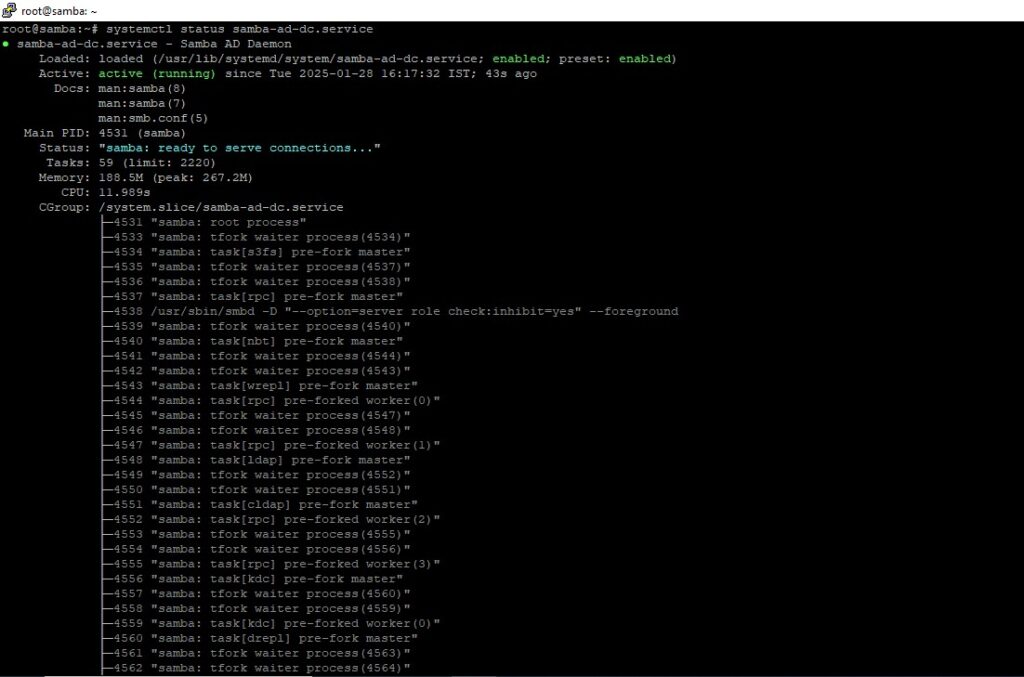
Use the netstat command to verify the list of all services necessary for Active Directory to function properly.
# netstat -tunlp | grep samba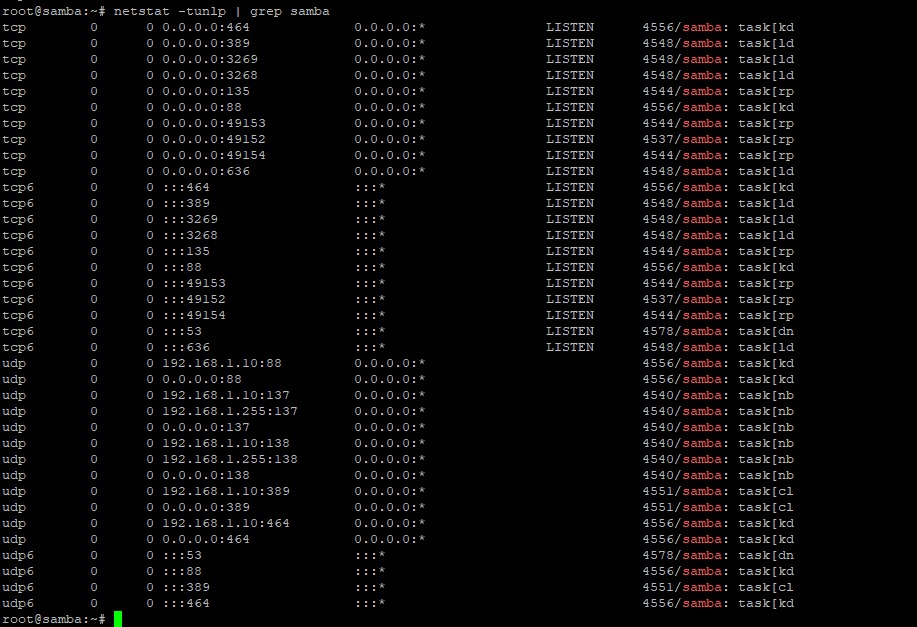
Final Samba Configurations
At this point, Samba should be fully operational at your location. The highest domain level Samba is currently emulating is Windows AD DC 2008 R2.
You can verify this using the samba-tool utility.
# samba-tool domain level show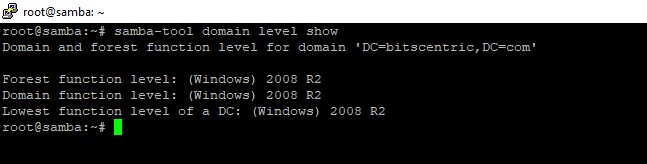
To enable local DNS resolution, you need to edit the network interface settings. Update the dns-nameservers field to the IP address of your Domain Controller (or use 127.0.0.1 for local DNS resolution). Additionally, set the dns-search field to match your realm.
# cat /etc/resolv.confFinally, test the DNS resolver by running queries and pings for key Active Directory Domain Controller (AD DC) records. Be sure to replace the domain name as needed in the examples below.
# ping samba
# ping samba.bitscentric.com
# ping bitscentric.com
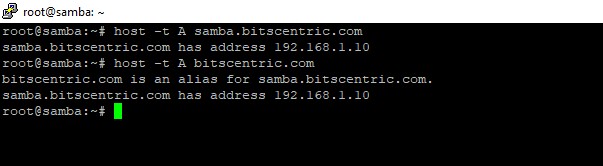
Run following few queries against Samba Active Directory Domain Controller
# host -t A samba.bitscentric.com
# host -t A bitscentric.com